Configuring Users Not Imported, Enabled, or Enrolled in Imprivata OneSign
This topic describes best practices for configuring Imprivata OneSign when some of your users are not yet imported, enabled, or enrolled in Imprivata OneSign (called "inactive users" in this topic).
NOTE: This topic assumes that all users authenticate with domain credentials (Microsoft Active Directory, for example), unless otherwise noted.
Select the computer policy of computers to be used by inactive users.
If the Computers in This Policy Are Used Only by Users with Domain Credentials
- Go to the General tab > Authentication.
- Set If Imprivata OneSign authentication fails, but Windows authentication succeeds, should the user be allowed to log in to the computer? to Yes
- Set Allow Users to Exit and Disable Agent? to No
-
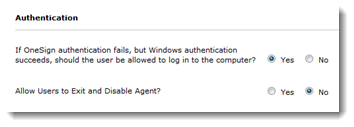
- Click Save.
If Computers in This Policy Are Used by Users Without Domain Credentials
Users who have no domain credentials must exit the Imprivata agent before accessing the desktop or an application.
- Go to the General tab > Authentication.
- Set Allow Users to Exit and Disable Agent? to Yes
-
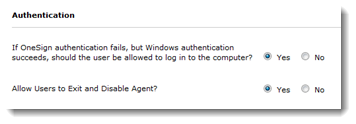
- Click Save.
CAUTION: If a user exits the Imprivata agent, auditing will be disabled. For more information about Imprivata OneSign feature support, see Supported Imprivata OneSign Features.
To configure authentication at shared workstations, go to the Shared Workstation tab > Windows Authentication section. Select one of the following options:
- Authenticate using OneSign — Inactive users will still be able to access the desktop with this selection.
-
BEST PRACTICE: This setting must be selected when either:
- Users have Imprivata Directory credentials but no domain credentials.
- The user's account is in a different domain than the thin client endpoint computer.
-
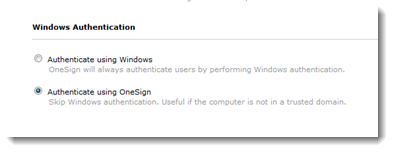
- Authenticate using Windows — Inactive users with domain credentials in the same domain as the thin client endpoint computer will still be able to access the desktop with this selection.
-

When a user logs into a thin client endpoint computer, Imprivata OneSign automatically connects to a virtual desktop environment (when assigned in user policy and enabled in computer policy). Inactive users also have Virtual Desktop Access, but they must select a virtual desktop and manually log in. You can configure this setting by computer policy:
- Go to the computer policy where Virtual Desktop Access is enabled, Virtual Desktops tab > Users that are not enabled option.
- Select a virtual desktop environment. You can choose from the virtual desktop environments already enabled for this computer policy.
-
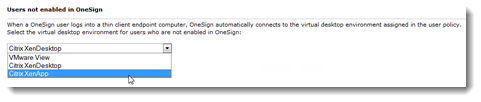
- Click Save.
See Expected Behavior for details on how this selection is presented during login.
NOTE: ProveID Embedded thin client firmware does not need to be updated to support the features described in this topic. Imprivata OneSign 4.9 Service Pack 1 or later is required.
Logging Into Virtual Desktops on Imprivata OneSign-Enabled Thin Clients
When logging into a thin client endpoint computer, inactive users with access to only one virtual desktop are automatically logged in. When the inactive user has access to multiple desktops, they are prompted to choose one:
- User 1 is not yet imported, enrolled, or enabled in Imprivata OneSign. He logs into a thin client endpoint computer.
- User 1 is prompted to choose a virtual desktop:
-

- The virtual desktop is launched. User 1 can proceed with his work.
NOTE: This behavior is only supported on Imprivata ProveID Embedded thin client endpoint computers. When logging into any other Imprivata OneSign-enabled shared workstation, inactive users must manually launch a virtual desktop.
Logging In, Logging Out, and Switching Between Users
Logging in, logging out, and switching between users is now supported for all users:
- User 1 is not yet imported, enrolled, or enabled in Imprivata OneSign. He logs into Computer 1.
- The desktop opens. User 1 can manually open and sign into virtual desktops and applications as needed.
- When User 1 is done with his work, he may lock the desktop with the hotkey, click the Imprivata OneSign icon in the Windows notification area to log out, or if they do nothing, Imprivata OneSign will secure Computer 1 when inactivity-based walk-away security activates.
- If User 1 logs into another computer, Imprivata OneSign will log out User 1 from Computer 1 and secure any applications they left unsecured on Computer 1, as configured in Imprivata OneSign's application profiles.
- User 2 is enabled in Imprivata OneSign. Regardless of how User 1 left the computer, User 2 can log into Computer 1 normally, with her username and password, or any authentication method configured in user policy and computer policy. All Imprivata OneSign features configured for this user and computer are supported.
Imprivata OneSign provides the same experience for users and inactive users, except where noted:
| Features | Users enabled in Imprivata OneSign | Users not imported, enrolled, or enabled in Imprivata OneSign |
|---|---|---|
| Windows Notification Area | User status is indicated by the Imprivata icon in the Windows notification area. |
User status is indicated in the Windows notification area: Endpoint computer is connected to the Imprivata appliance:
Endpoint computer is not connected to the Imprivata appliance:
|
| Walk-Away Security | Inactivity-based presence detection is configured in computer policy. | Inactivity-based presence detection is supported. |
| Single Sign-On | Supported with the Single Sign-On option for the Imprivata OneSign license. | Single Sign-On is not supported. |
| Hotkey Log Out | Logging out of Imprivata OneSign with the hot key is configured in computer policy. | Logging out of Imprivata OneSign with the hot key is supported. |
| Authentication Methods | Authentication methods are configured in user policy and computer policy. |
Users must use their username and password to log in. Other authentication methods such as proximity card, fingerprint, or token are not supported. NOTE: You customize the error message that appears when an inactive user taps a proximity card at an endpoint computer. |
| Application Logoff and Shutdown | To protect patient health information, applications can be profiled to log off and shut down when a user is done. | Application log off and shut down settings are supported when any user logs in or out. |