Extension Objects
Extension objects allow Imprivata Enterprise Access Management to extend beyond its base capabilities to support external software tools. You assign Extension Objects to computers using computer policies, which are detailed in Creating and Managing Computer Policies.
NOTE: Extension objects are unrelated to the Enterprise Access Management extension that is installed in Google Chrome to enable single sign-on. See Support for Applications that Run in Google Chrome.
Enterprise Access Management supports three extension objects, available from the Extensions tab of the Computer policy page in the Imprivata Admin Console:
-
Using the Carefx Extension Object — Synchronize user identity with the Carefx Application Context Manager.
-
Using the Managed Exit for MEDITECH Extension Object — Manage a graceful exit of MEDITECH applications run through Forward Advantage’s MEDITECH MEM API.
-
NOTE: This extension object only applies if you are providing Single Sign-On (SSO) to Meditech applications through Enterprise Access Management.
-
Using the Procedure Code Extension Object — Manage the execution of procedure code triggered by pre-defined agent and application events.
Imprivata is a Carefx Infrastructure Partner, and Enterprise Access Management is fully integrated with the Carefx Fusion Context Channel software and Fusion Context Manager CCOW solution.
Fusion Context Channel connects Enterprise Access Management to Fusion Context Manager. When users authenticate to Enterprise Access Management, Enterprise Access Management authenticates them into the full Fusion Context Manager experience. This works on all computers that have a Fusion client installed and an Imprivata agent installed. It does not matter which kind of Imprivata agent is installed.
No scripting or other modifications are required. To use Enterprise Access Management with Fusion Context Channel and Fusion Context Manager, just enable the Carefx extension object.
NOTE: You can enable or disable the Carefx extension object in a computer policy, but you cannot edit it.
Enterprise Access Management integrates with Fusion Context Manager by synchronizing the context manager with the user ID. When a user logs into a computer with an Imprivata agent and a Fusion client installed, if the Carefx extension object is enabled, then Enterprise Access Management runs a Carefx synchronize action with Fusion Context Channel. The synchronize action then sets the user ID into the CCOW context.
Imprivata and MEDITECH, working together with Forward Advantage, have produced an extension object designed to manage exit functions from MEDITECH applications when switching users on a shared workstation.
NOTE: This extension object only applies if you are providing SSO to MEDITECH applications through Enterprise Access Management Single Sign-On.
Procedure codes are command sequences or more complex JavaScript, PowerShell, or VBScript scripts triggered by pre-defined agent and application events.
When using PowerShell, consider the following:
-
Script Block Logging can expose sensitive information, such as hard-coded credentials. To prevent the unintended exposure of sensitive information, disable Script Block Logging. If you must enable Script Block Logging, Microsoft recommends enabling Protected Event Logging. For more information, see the Microsoft documentation.
-
The
Get-Credentialcommand is not supported.
When you create a procedure code, you use a chooser to select events that will trigger the code, and then write the code in an edit box beneath the events chooser. The Imprivata agent and application events and the Enterprise Access Management variables are provided in live glossary links.
You can define single events, use an OR function to define alternative events, and use a PAUSE/EXCEPT combination to define a canceling event.
Microsoft has announced the deprecation of VBScript. Microsoft has not announced a release date on which VBScript will be retired, instead stating that VBScript will be available as a feature on demand before being retired in a future Windows release. While Imprivata procedure code extension objects continue to support VBScript, it is recommenced that you create new event triggers using a supported scripting language, such as JavaScript or PowerShell, while planning for the retirement of VBScript.
A VBScript to map to a specific drive depending on who logs into a workstation: Each time a user logs into the workstation, the script executes to ensure the user has access to the correct network drive. In this example, the user login is the event, and the mapping is handled by a VBScript created by an Administrator.
A VBScript to unmap the drive when the user logs out or is disconnected: When any user logs out of the workstation, the desktop locks and the drive mapping is deleted. In this example, the desktop lock is the event, and the mapping and unmapping is handled by a VBScript created by an Administrator.
You create, edit, and delete procedure codes from the View/Edit link of the Procedure code section of the Extensions page from the gear icon.
Creating a Procedure Code
To create a new procedure code:
-
Click Add.
-
Specify the conditions under which the procedure code is to be executed . See Specifying the Conditions.
-
Enter the code. See Entering the Code.
Editing a Procedure Code
To edit an existing procedure code, click on its name and make your changes just as if you were creating a new procedure code.
Deleting a Procedure Code
To delete one or more procedure codes:
-
Select the names of the codes to be deleted.
-
Click Delete.
The first step when setting up a procedure code is to specify the conditions that trigger it. Conditions are built from events arrayed in a logic tree as shown in the following image:
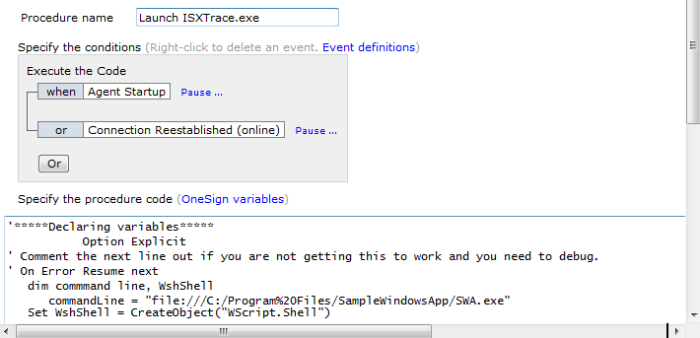
Events that occur at the agent level, regardless of what applications may be running, are global events. Events that are triggered by an application starting or shutting down, or by a specific window within a specific application, are application events. Application events are supported in Enterprise Access Management with SSO only.
To specify conditions that will trigger a procedure code:
-
Select a global event to trigger the procedure code, or scroll to the bottom of the Global Events list and select Application Events to open a drop-down list that shows all profiled applications. When you select an application, a new drop-down list opens showing application events. Select an application event to trigger the procedure code. Application events are available only with the SSO option.
-
If the event should always trigger the procedure code, then enter the code.
-
If there are additional events that may trigger the same code, then click Or and select additional global and application events as needed.
-
To enter an exception that can cancel the procedure code, click Pause... and enter the pause duration in seconds, and then fill in the Unless conditions in the same way. Execution of the procedure code is delayed for that period (counting from the triggering event) while the agent watches for the canceling event to occur:
-
If the Pause time elapses without the canceling event taking place, then the procedure code is executed.
-
If the canceling event occurs, then the procedure code is not needed.
Procedure codes are triggered by events. Use the Events Glossary to be certain of the events that will trigger the procedure code. There are two types of events:
-
Global Events for Procedure Codes — The global events in the following table are triggered by Imprivata agent activities and apply without regard to any running applications. Global events are useful for Procedure Codes invoked by user or computer workstation actions.
-
Application Events for Procedure Codes (SSO Only) — The application events in the second table are triggered by Enterprise Access Management-recognizable events from specific applications. Application events are monitored only when you have Enterprise Access Management SSO installed.
Global Events for Procedure Codes
Application Events for Procedure Codes (SSO Only)
The procedure code can be BAT files and commands to be executed from the command line, or more complex scripts written in JavaScript, PowerShell, VBScript, or WSH, supplemented with Imprivata variables.
NOTE: While procedure codes continue to support the use of VBScript, Microsoft has announced their deprecation. It is recommenced that you create new event triggers using another supported scripting language, while you plan for the retirement of VBScript.
The following image shows an example of the Edit Procedure Code -- Webpage Dialog:
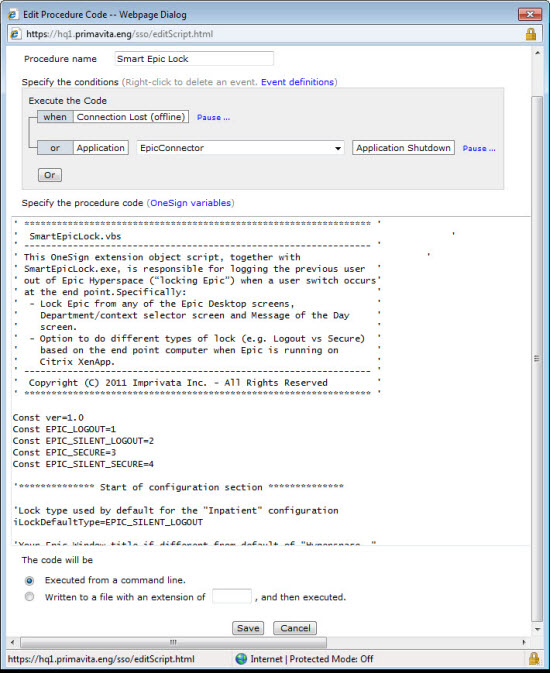
The Variables Glossary
When you enter the procedure code, use the Imprivata variables available from the Variables Glossary.
NOTE: Imprivata APG keystroke codes are not usable with procedure codes.
Select if the procedure code is to be executed from the command line or saved to a file as shown in the following image:
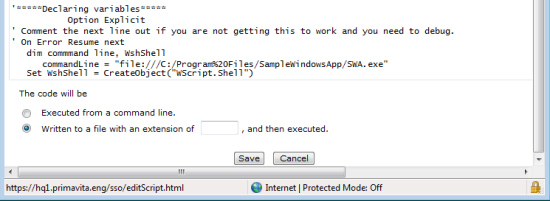
- Procedure codes run from the command line must use DOS commands, which are limited to a single line of code.
- Procedure codes saved to a file can be complex scripts written in JavaScript, PowerShell, or VBScript. These procedure codes are saved in a TEMP folder only until executed. At runtime, the variables are replaced with in-memory values. At runtime the code is temporarily saved to disk for execution and then deleted when execution terminates.
- The Imprivata agent uses the Windows Shell to open the saved file for execution, relying upon the file extension to identify how to execute it.
- The procedure code cannot be used until it is enabled in a computer policy; see Enabling Extension Objects in Computer Policies.
PowerShell Script Block Logging can expose sensitive information, such as hard-coded credentials. To prevent the unintended exposure of sensitive information, disable Script Block Logging. If you must enable Script Block Logging, Microsoft recommends enabling Protected Event Logging. For more information, see the Microsoft documentation.
If you are deploying a PowerShell script that requires an execution policy, configure the following registry key on your Windows endpoints. The Imprivata agent enforces the execution policy that the registry key specifies, regardless of the default execution policy scope on the local endpoint. Consider the following:
-
Windows 11 23H2 and earlier — The default value for all scopes is
Undefined. If the default values are unchanged, and the registry key is not configured, the PowerShell script does not run. -
Window 11 24H2 — The default value for
LocalMachineisRemoteSigned. All other scopes default toUndefined. If the default values are unchanged, and the registry key is not configured, the PowerShell script runs with theRemoteSignedexecution policy.
| Name | Type | Location | Execution Policy | Value |
|---|---|---|---|---|
|
PSExecutionPolicy |
DWORD |
HKLM\Software\SSOProvider\ISXAgent |
The default value. No execution policy is specified. | 0 |
| Restricted | 1 | |||
| AllSigned | 2 | |||
| RemoteSigned | 3 | |||
| Unrestricted | 4 | |||
| Bypass | 5 | |||
| Default | 6 | |||
| Undefined | 7 |
The shared secret generates an 256 bit AES encryption key used to establish trust between the Imprivata appliance and the third party application.
Details of the encryption key:
Salt: SSOENCPWD
Algorithm: AES256
Key size: 256 bits
Block size: 16 bytes
Cipher mode: CBC
Padding: PKCS#7
You must also enter this secret in the third party application.
To set the shared secret:
-
Click Set.
-
Enter and confirm the shared secret. The shared secret should be between 8 and 128 characters in length.