Single Sign-On Security Settings
Single Sign-On is a balance of user convenience against network security. When you deploy an APG application profile to users, you should pay careful attention to security settings.
NOTE: Password Self-Service is not the same as a password policy.
Imprivata Enterprise Access Management offers four ways to enforce security for individual applications, as shown in the following sections.
You can let users edit their APG application credentials in the password manager or in Password Self Services by checking Allow users to modify and delete application single sign-on credentials. For example, the following image shows that this application user can edit his application credentials:
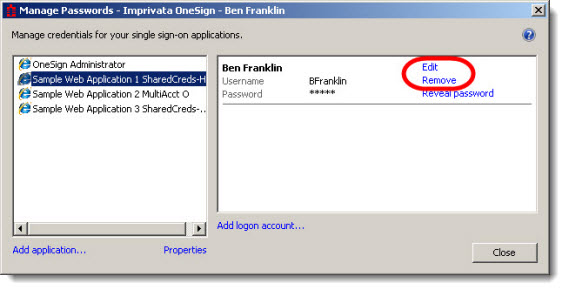
Users can edit the application display name, username, and password. To make this feature more secure, you can require the user to answer security questions to reveal application credentials from the Self Service Portal. In the Password Manager, the password remains obfuscated unless the application also permits passwords to be revealed. See Allowing Users to Reveal Application Passwords
If you want to permit users of this application to reveal their passwords in the password manager or in the Password Self Services feature, select Allow users to reveal application passwords. For example, in the following image this application user can reveal his application password:
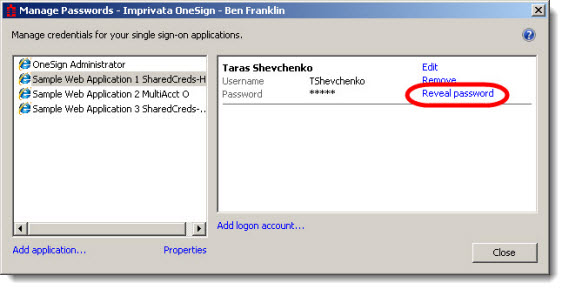
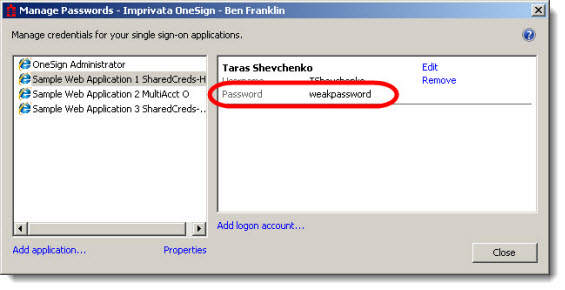
When a user clicks Reveal password an authentication screen opens. The user is required to enter credentials to prove their identity. After the user has satisfied the requirement, Enterprise Access Management reveals the password. The password remains revealed until the user closes the password manager. For example, in the following image the application user's application password is revealed:
Enterprise Access Management monitors user enrollments and authentication to applications. When shown the Multiple Accounts or Enterprise Access Management Credential Enrollment Windows, users can have the option to cancel the operation, bypassing Single Sign-On. The following image displays the message stating that the user cannot bypass Single Sign-On (SSO) for this application:
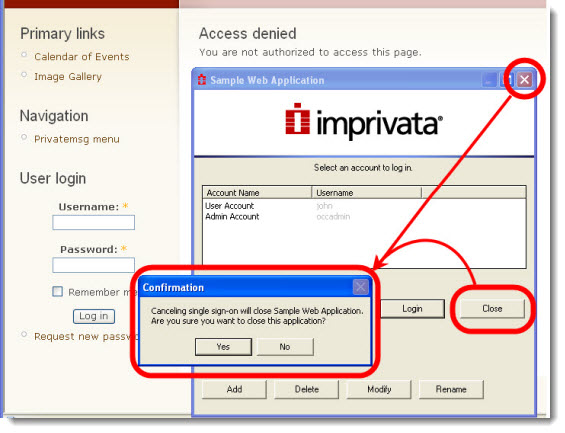
To prohibit users from bypassing SSO for this application, deselect the option as shown in the following image:
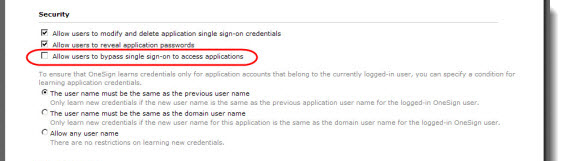
If Allow users to bypass single sign-on to access applications is not selected, and a user clicks Close, Enterprise Access Management terminates the application. If you have configured a shutdown sequence, then Enterprise Access Management runs that sequence.
If a shared workstation is not secured when a user (User A) walks away, there is a risk that another user (User B) uses the workstation without logging into Enterprise Access Management as himself. While User B is using the workstation, if an application goes into Learning mode (for example, if proxy failed or User A was not yet enrolled in the application), then User B's credentials will be learned under User A's name. To avoid this, Enterprise Access Management offers several methods of securing unattended workstations. See Configuring Walk-Away Security for Unattended Workstations
To ensure that Enterprise Access Management learns credentials only for application accounts that belong to the currently logged-in user, you can specify a condition for learning application credentials in the Security section of the application deployment page or the Credential Store page as shown in the following image:
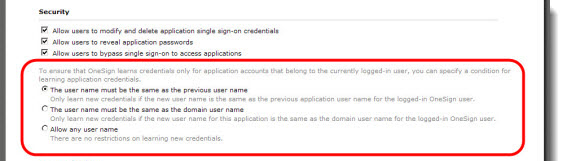
This includes three options:
The User Name Must Be the Same as the Previous User Name
You can prevent the agent from learning new credentials, if the user name is not the same as the previously recorded user name for the same application.
If the application user name is not always the same as the user's domain user name, then select this restriction. When this restriction is set:
-
Enterprise Access Management only re-learns credentials for an application if the application user name does not change for that login account.
-
This restriction is enforced only after the user is enrolled for the+ application. To avoid learning credentials for the wrong user, be sure that shared workstation users go through a managed enrollment process before they start using single sign-on.
-
If the application uses its own login screen (no Credential Enrollment Window is configured), when the user logs into the application with a user name that does not match the previously learned user name for that application account for the logged-in user, Enterprise Access Management ignores the credentials. Enterprise Access Management informs the user that the credentials were not captured because the user name did not match the previous user name.
-
If the application uses a Enterprise Access Management Credential Enrollment Window, then the previously learned user name for that application account for the logged-in user is displayed in the credential enrollment dialog. The user name is read-only.
-
If the user is allowed to have Multiple Accounts for that application, then the user is free to add additional accounts using the Multiple Accounts window without any restrictions, but modifying an account using the Multiple Accounts dialog needs to meet the credential learning restriction.
-
The Imprivata password manager warns the user, but does not otherwise enforce this restriction. This provides an "escape hatch" to add or edit credentials if necessary when this restriction is in place.
The User Name Must Be the Same as the Domain User Name
If the application user name is the same as the user’s domain name for all users, then select The user name must be the same as the domain user name.
-
This restriction ensures that the application's credentials are learned for the correct user during first-time enrollment, as well as any subsequent credential learning event.
-
If the application uses its own login screen (no Credential Enrollment Window is configured), when the user logs into the application with a user name that does not match the domain user name of the currently logged-in user, Enterprise Access Management ignores that set of credentials. Enterprise Access Management informs the user that the credentials were not captured because the user name did not match the network user name.
-
If the Enterprise Access Management Credential Enrollment Window is configured, then the domain user name of the currently logged-in user is displayed in the Credential Enrollment Window. The user name is read-only.
-
If this restriction is set, and the user is allowed to have Multiple Accounts for that application, then any SSO account added using the Multiple Accounts window for that application requires that the user name for the account that is being added must be the same as the user's domain user name.
-
The Imprivata password manager warns the user, but does not otherwise enforce this restriction. This provides an "escape hatch" to add or edit credentials if necessary when this restriction is in place.
NOTE: This risk of learning credentials for the wrong user does not apply to applications that share credentials with the domain because Enterprise Access Management does not learn that application's credentials through the single sign-on process.
Allow Any User Name
There are no restrictions on learning new credentials with this option.