NHS Spine Support for Imprivata ProveID Embedded
Support for Spine applications reduces the time users must wait when re–authenticating to those applications during their shift.
After users authenticate for the first time, the appliance manages subsequent Spine authentication requests. Delegating the requests to the appliance removes the delays associated with network factors, such as load and latency, that can exist between your enterprise and the Spine.
This topic details how to enable support for NHS Spine applications that are accessed on a published desktop from Imprivata ProveID Embedded endpoints. Imprivata ProveID Embedded supports the Imprivata Spine Combined Workflow on the following published desktops:
-
VMWare View Desktop
-
Citrix XenDesktop
-
Citrix XenApp
NOTE: For more information on configuring Imprivata Virtual Desktop Access for a published desktop, see Installing and Configuring Support for Omnissa Horizon Virtual Desktops, Configuring Citrix XenApp Published Desktops, and Configuring Imprivata Virtual Desktop Access with Citrix XenDesktop.
Before You Begin
Familiarize yourself with the expected end user workflow, requirements, and supported authentication methods.
The following steps detail the authentication workflow when the user policy is configured for Spine support:
-
At the beginning of the shift, the user authenticates to Imprivata Enterprise Access Management on endpoint 1 using two–factor authentication. The published desktop is launched.
-
The user inserts their Spine card into the reader and opens a Spine application. The user is prompted for a passcode.
-
The user enters the passcode and is authenticated to the Spine. The Imprivata grace period is established. During the grace period, the appliance manages the authentication request.
-
The user closes the Spine application and removes their Spine card.
-
The user returns to endpoint 1 and opens a Spine application. The user is not required to insert their Spine card and is not prompted for a passcode.
-
The user logs out of endpoint 1.
- During the same shift, the user authenticates to Enterprise Access Management on endpoint 2 using two–factor authentication and opens a Spine application. Although the user has moved to a different endpoint, inserting a Spine card and entering a passcode is not required.
The appliance continues to manage the authentication request during the grace period.
The following Imprivata licenses are required to enable the Spine authentication workflow:
-
Authentication Management
-
Single Sign–On
-
Virtual Desktop Access
-
Spine Combined Workflow
-
(Optional) Fingerprint
Support for the Spine Combined Workflow is limited to 64–bit HP and IGEL thin client devices. See the Enterprise Access Management - SSO Supported Components in the Imprivata Environment Reference to confirm that your devices are supported.
The following authentication methods are supported when authenticating to the Imprivata ProveID Embedded endpoint:
-
Fingerprint + Imprivata PIN
-
Fingerprint + password
-
Proximity card + Imprivata PIN
-
Proximity card + password
-
Proximity card + fingerprint
-
Proximity card + fingerprint or password
-
Proximity card + fingerprint or Imprivata PIN
NOTE: By default, Imprivata passes the user name/password to the VDI server.
Configuring NHS Spine Support for Imprivata ProveID Embedded
Complete the following steps to enabled NHS Spine support.
The NHS Digital Identity Agent version 2.0 or later must installed on all Windows virtual machines that are being delivered as published desktops.
After installation, verify that the NHS Digital Identity Agent is installed to the default location. The default installation location for the NHS Digital Identify Agent is:
-
32–bit —
Program Files\HSCIC\Identity Agent -
64–bit —
Program Files (x86)\HSCIC\Identity Agent
If the NHS Digital Identity Agent is not installed to the default location, complete the following:
- Add the IAFilename value to the ISXAgent registry key. The registry key is installed with the Imprivata agent and is located at:
HKEY_LOCAL_MACHINE\SOFTWARE\SSOProvider\ISXAgent
-
Configure IAFilename with a Data Type of REG_SZ and set the value to the fully qualified path of the NHS Digital Identity Agent executable.
Configuring Spine support requires that you:
- Enable the user policy for Spine applications.
- Verify that the user policy is configured for two–factor authentication. NHS guidelines require two–factor authentication.
- Specify an Enterprise Access Management grace period of up to 10 hours. After users authenticate for the first–time, the grace period duration determines how long the appliance manages subsequent Spine authentication requests.
BEST PRACTICE: Specify an Enterprise Access Management grace period that corresponds to the typical length of the shift, and use this value to control when users must re-authenticate to the Spine. When the Spine Combined Workflow is enabled, the grace period must fall within the duration of the grace period that the Spine Security Broker specifies.
To configure Spine support:
- From the Imprivata Admin Console, open the user policy you want to edit or create a new user policy (Users menu > User policies).
- On the Authentication tab, go to the Spine Combined Workflow section.
- Select Allow persistence of Spine Combined Workflow session and specify the Grace period for Spine persisted data.
- Save and assign the user policy.
Enterprise Access Managementcloses all known Spine applications on user switch:
- A known Spine application is one that directly uses the Identity Agent ticket API to establish the connection with the NHS Digital Identity Agent.
- An unknown Spine application is one that indirectly uses the Identity Agent ticket API to establish the connection. For example, a web browser–based application may use a program file, such as
jp2launcher.exe, to establish the connection.
An Enterprise Access Management procedure code extension object is required to close unknown Spine applications on user switch. For more information on procedure codes, see Extension Objects.
Manage Access for Endpoint Authentication USB Devices
The following sections detail the types of USB redirection used to redirect authentication devices to the published resources.
NHS applications require the use of a Spine smart card. Third–party USB redirection is used for the smart card reader and must be configured using the thin client administrative utility.
The Imprivata virtual channel is used to access all proximity card and fingerprint readers. No additional configuration is required, unless your environment includes the IMP–MFR–75 reader.
The IMP–MFR–75 reader can function as a smart card reader or a proximity card reader. If this type of reader is deployed, disable the smart card functionality. Disabling the smart card functionality lets Imprivata ProveID Embedded handle the proximity card functionality, including authentication and tap–to–lock through the Imprivata Virtual Desktop Access session.
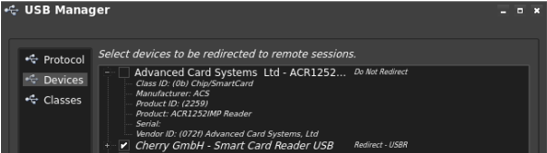
To disable the smart card functional, use thin client administrative utility to block the IMP–MFR–75 from being redirected with USB redirection.
The following is an example of disabling the IMP–MFR–75 on an HP ThinPro device.
Click to enlarge
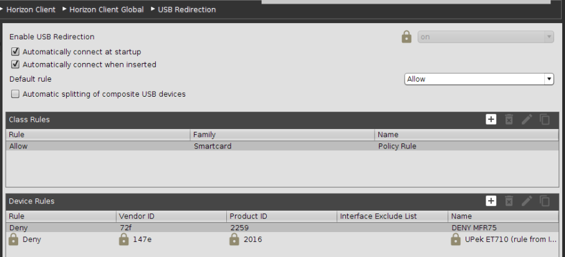
The following is an example of disabling the IMP–MFR–75 on an IGEL device for VMWare.
Click to enlarge
Reporting Spine User Activity
The Spine Combined Workflow report provides information about users and the authentication events related to their Enterprise Access Management Spine session, including:
- When Enterprise Access Management created a Spine session on behalf of an authenticated user.
- The number of times that the Spine session was used to re-authenticate the user.
- The number of times the Spine session was not used to re-authenticate the user because the two–factor authentication requirement was not met.
- When an Administrator deleted a Spine session of an authenticated user.
NOTE: For more information about creating a report, see Using Reporting Tools.
Managing a Spine Session
After a user authenticates for the first time, the Enterprise Access Management grace period duration determines how long the appliance manages subsequent Spine authentication requests.
There are times, however, when the persisted session and its grace period must be deleted or reset.
Delete a Spine session when it should no longer be associated with the user. For example - a user has reported a Spine card lost or stolen.
To delete a Spine session:
- In the Imprivata Admin Console, go to the Users menu > Users page.
- Search for the required user and click the user name to view their Imprivata account information.
- Go to the Spine Combined Workflow associated tickets section and click Delete Ticket. The session is immediately ended.
Users can reset their own session. For example, a user with multiple roles must reset their Spine session to switch from their current role to another.
To reset the Spine session:
- From a computer on which the user has authenticated to Enterprise Access Management, Ctrl + click the Imprivata agent icon, and click Reset Spine session. The session is immediately ended.
- Instruct the user to authenticate to the Spine as normal. A new Spine session is created and the grace period is reset.
Modified Registry Settings
Enabling Spine support modifies, if necessary, the following NHS Digital Identity Agent registry settings:
- CardRemovalCheck
Default value: true
Modified value: false
- SessionLockPersistence_Enabled
Default value: false
Modified value: false
- IdleWaitPeriodInSeconds
Default value: 1800
Modified value: 36000
NOTE: For more information about these registry settings, see the HSCIC Identity Agent Administrators Guide.