Authentication for Smart Cards or USB Tokens with External Certificates
Smart cards provide two-factor authentication by combining a user PIN with a pre-programmed smart card. This topic describes smart cards with certificates issued by an external agency. Imprivata Enterprise Access Management authenticates users through a third-party application rather than Windows. For more information see Enterprise Access Management Authentication for Smart Cards or USB Tokens with Microsoft Active Directory (AD) Certificates.
You assign smart card authentication (and all other authentication methods) through the Enterprise Access Management User Policies that you assign to each user.
Enforcing Smart Card Certificate Validity
You have the option to prohibit authentication with these smart cards if the card certificate has expired. To do this, select it under Options.
Smart card certificate information is displayed in and can be deleted from the user record as shown in the following image:

Revoking Smart Card Authentication Privileges
Revoke smart card authentication privileges through the Enterprise Access Management User Policies that you assign to each user. Create a different user policy and assign it to the user.
You can enforce the use of smart cards with an external certificate for desktop access in specific Computer Policies, overriding the User Policy.
- In the Imprivata Admin Console, go to your computer policy > Override and Restrict tab > Desktop Access Authentication Restrictions.
- Select Restrict user policy.
-
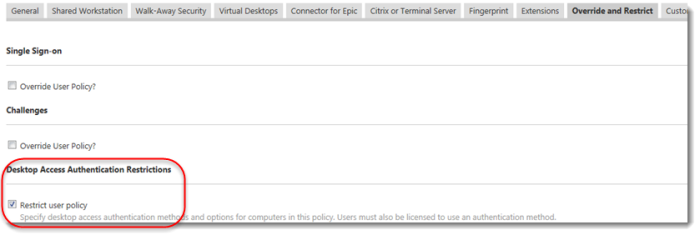
- Scroll down and select Smart Card or USB token using external certificate. Allow temporary use of conditional primary methods, if needed.
-

- (Optional) In the section Authentication method options > Smart card using external certificate, select Allow smart card enrollment and authentication only while certificate is valid.
-
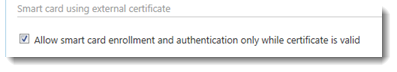
- Click Save.
Smart cards with externally issued certificates cannot be used for authentication to Enterprise Access Management until the card certificate has been mapped to a user during an enrollment process. Enrollment occurs during the login/unlock process.
- The user inserts a smart card to authenticate to the network. The PIN dialog opens.
- The user enters a valid PIN.
- Enterprise Access Management does not recognize the certificate as one mapped to a user. Enterprise Access Management displays the Enroll smart card login or unlock dialog, and prompts the user to enter a valid domain password:
- The user enters username and password. The PIN dialog opens a second time.
- The user enters a valid PIN. Enterprise Access Management validates the certificate and maps the User Principal Name from the certificate to the user.
To log in, the user inserts the card or token into the reader and then enters the associated PIN. The user’s Enterprise Access Management experience is no different from users with any other authentication method.
The authentication process is straightforward. To authenticate via smart card:
- When the Windows Log On screen opens, insert the smart card into the smart card reader. The Imprivata Smart Card Login window opens.
- Enter your PIN to enable the smart card. Repeated failure to correctly enter the PIN may disable the smart card.
When you are authenticated, the login window closes.
If you have multiple authentication options, you first see the Imprivata login screen. To log in by smart card, ignore the listed options and insert your smart card as described in the preceding procedure.