Enterprise Access Management Authentication for Smart Cards or USB Tokens with Microsoft Active Directory (AD) Certificates
Imprivata OneSign supports smart card and smart USB token authentication via the Windows Local Security Authority and Kerberos Security. Smart card and USB token authentication use the same Imprivata OneSign settings.
Smart cards and smart USB tokens provide two-factor authentication by combining a user PIN with a pre-programmed smart card or USB token. Smart cards are valid until the expiration date of the digital certificate on the card, normally valid for two or more years.
In SSO environments, smart card authentication grants network access and an SSO session in a single step. Smart card-enabled users authenticating to Imprivata OneSign use a smart card and associated PIN. Imprivata OneSign makes no difference to the user experience of logging into Windows.
When you authorize users for authentication with smart cards that use Active Directory certificates, you must have a Kerberos Keytab File uploaded to the Imprivata OneSign server as detailed in Creating a Kerberos Keytab File.
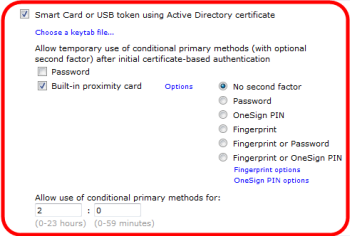
Conditional primary methods are primary authentication methods that can be used only under the condition that the user authenticated with the smart card within the allowed period.
This topic describes smart cards and USB tokens with certificates issued by Microsoft Active Directory (AD). Smart cards/USB tokens with certificates issued by an external agency are described in Authentication for Smart Cards or USB Tokens with External Certificates.
For a complete list of supported smart cards, see Imprivata OneSign Supported Components.
NOTE: There is no separate enrollment step for Active Directory smart cards. Enrolling for smart card/USB token use in Active Directory automatically enrolls the user for use in Imprivata OneSign.
To create and run an Enrollment report, in the Imprivata Admin Console, go to Reports > Add new report.
Enterprise Access Management supports smart card authentication via the Windows Local Security Authority and Kerberos. PC/SC-compatible smart card/USB token technology is provided with MS Active Directory. The PKI infrastructure must be installed to support Kerberos security and smart card authentication.
Complete the following steps to configure Enterprise Access Management to work with your Microsoft Active Directory Server smart card/USB token system.
-
Network Page — Before you begin, it is important to be sure the appliance is configured to communicate with the NTP time server on the domain controller that supports the smart card users. Set this on the NTP tab of the Network page on the Imprivata Appliance Console.
-
Create a Keytab File and Upload it to the Imprivata Appliance — Configure the Microsoft Active Directory Server to recognize Enterprise Access Management.
-
Assign Smart Card/USB Token Authentication Privileges — Create or edit a security policy that allows smart card use. The following image shows a user policy that allows Smart Card/USB token authorization:
-
NOTE: Refer to your Microsoft Active Directory Server documentation for additional information about Kerberos v5 security.
You assign smart card/USB token authentication (and all other authentication methods) through the user policies that you assign to each user.
You can revoke smart card/USB token authentication privileges through the user policies that you assign to each user. Create a different user policy and assign it to the user.
User policies are detailed in Creating and Managing User Policies.
To log, the user inserts the card or token into the reader and then enters the associated PIN. All smart card and smart USB token authentication to the domain is handled by the Microsoft GINA, but the user’s Enterprise Access Management experience is no different from users with any other authentication method.
The authentication process is straightforward. To authenticate via smart card:
-
At the Windows Log On screen, insert the smart card into the smart card reader.
-
Enter your PIN to enable the smart card. Repeated failure to correctly enter the PIN might disable the smart card.
When you are authenticated, the login window closes.
If you have multiple authentication options, you first see the Imprivata login screen. To log in by smart card, ignore the listed options and insert your smart card as above.
Remote Third-Party Smart Card Authentication via RDP
For remote external-certificate smart card authentication via RDP, see Remote Device Authentication to Imprivata Enterprise Access Management for SSO.