Authenticate to Microsoft Apps on iOS Devices
NOTE: This topic applies to iOS devices. To configure authentication to Microsoft apps on Android devices, see Authenticate to Microsoft Apps on Android Devices.
Imprivata Mobile Access Management integrates with Microsoft in several ways to streamline sign in and out:
-
Two-tap sign-in: eliminate dozens of key presses at the start of each shift, skip realm discovery, seed the users’ email addresses, and autofill passwords
-
Automatic sign-out: Cleanly close all apps supporting the Microsoft Authentication Library (MSAL) and shared device mode
These benefits save significant time for your workers each day, increase mobile adoption, and remove private data once no longer needed. As a secondary benefit, password management allows your organization to increase password complexity, and increase security, without creating additional burden on your staff.
Requirements
There are strict requirements, which may limit when this feature may be used:
-
Microsoft’s apps must be aware of Microsoft’s Shared Device Mode.
-
For supported apps, see your Microsoft documentation.
-
-
Devices must be in Microsoft’s shared device mode, which typically requires touching each device to authenticate once as an Azure admin user. If using Microsoft Intune, the process is streamlined significantly, however you will need to erase and re-provision each device.
Expected Behavior
-
On device check out, users will see the standard Check Out screen with their name.
However, this screen now includes a blue button to continue to sign into Microsoft’s authentication system.
-
Users may swipe up to skip Microsoft authentication, in which case they will be prompted when opening their first Microsoft app. If they do tap the button, they are presented with a standard Microsoft authentication screen, with your organization’s branding.
-
Note that Mobile Access Management has already added the user’s UPN (email address) so the system skips this initial screen and routes directly to password entry. Users can select the correct credentials using Autofill selection.
TIP:Use Azure Conditional Access to disable MFA for shared devices.
-
Users open the Microsoft Teams app to complete the sign in. Microsoft Teams will not recognize the login until the app is opened once. When opened, Teams does not prompt for a login.
-
When the device is returned to the Launchpad, Mobile Access Management automatically signs out of Microsoft Teams and the Microsoft authentication system with no prompt and no action required by the user.
There are several tasks required to set up this behavior.
Microsoft’s Shared Device Mode
Unlike most apps, Microsoft uses device-wide authentication, saving an authentication token (for iPhones, this is to the iPhone’s keychain). This way, a single sign-in can be shared among multiple apps. Similarly, a single sign-out should cause all apps in the group to be signed out. But Microsoft’s authentication system is generally optimized for 1:1 mobile devices.
To modify these behaviors for shared use, Microsoft has introduced its shared device mode. Microsoft’s shared device mode modifies the Microsoft sign-in workflow to be more suitable for shared devices. In addition, apps can be built to be aware of Microsoft’s shared device mode, and can modify their behavior to be optimized for shared device workflows.
Microsoft Intune Only - Create a DEP Profile for Shared Mode
For more information, see the Microsoft documentation.
This is available only for DEP devices.
-
Open Devices > iOS/iPadOS > iOS/iPadOS enrollment > Enrollment program tokens > (token name) > Profiles.
-
Create a new profile for iOS/iPadOS.
-
Enter a name for the profile, such as "Shared Mode."
-
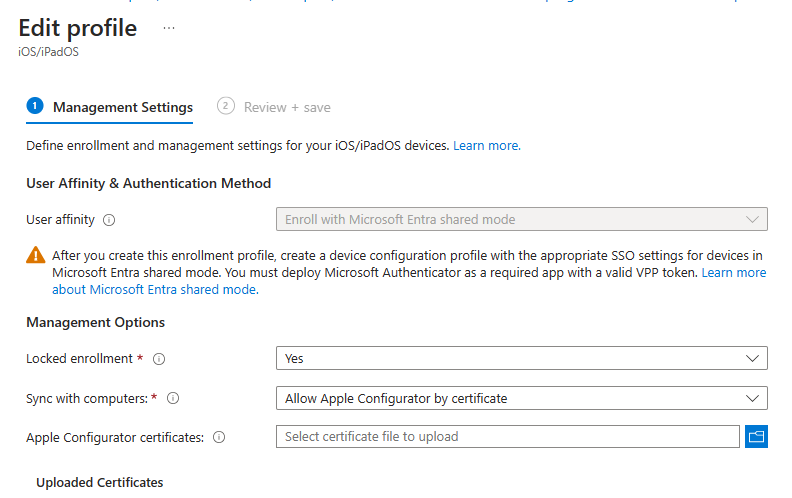
In the User affinity & Authentication Methods section, select Enroll with Microsoft Entra ID shared mode from the list.
Click to enlarge
-
In the Management Options section, configure the following:
-
For Locked enrollment, select Yes.
-
Set Sync with computers to Allow Apple Configurator by certificate and upload your Mobile Access Management supervision identity here.
Remember to rename the supervision identity from ".crt" to ".cer".
-
-
Assign your shared iOS devices to this new enrollment profile.
Then erase and re-provision your devices. Intune pushes the required configuration to the Authenticator app to enable shared device mode.
Create a dynamic Microsoft Entra group using the enrollmentProfileName property to automatically group devices that enroll with a specific enrollment profile. In this case, we want to group devices that are in shared device mode and enrolling with the profile you created in Step 1.
Include these configurations when creating your dynamic group:
-
Group type: Security
-
Membership type: Dynamic Device
Add a dynamic query with the following rule:
-
Property: enrollmentProfileName
-
Operator: Equals
-
Value: Enter the name of the enrollment profile you created for devices in shared device mode.
Microsoft requires its Authenticator app to be installed to enable shared device mode.
For iOS devices, "purchase" the app (for free) using Apple Business Manager and distribute it to all your shared devices.
-
Assign the Microsoft Authenticator app to targeted devices. Assign the app as required to All devices.
-
Add the enrollmentProfileName assignment filter you created in Step 3.
Non-Intune - Authorize Microsoft Authenticator App
Skip this task if you use Microsoft Intune as your MDM.
-
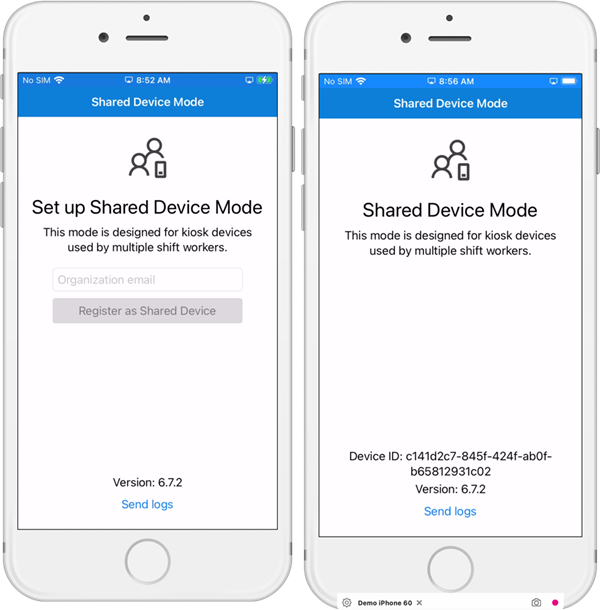
Open the Microsoft Authenticator app on each device. The app prompts you to set up Shared Device Mode and requests an Organization email and password. These credentials must be for a user with Azure Cloud Device administrator privileges.
-
You must enter these credentials once, on every device, but the registration persists until you erase the device. This is an important step that cannot be automated at this time.
Click to enlarge
Create the Enterprise SSO Profile
For all MDMs, you must create and deploy a specialized configuration profile to enable in-app authentication. This profile intercepts the standard Microsoft authentication workflow, and substitutes an authentication extension embedded in the Microsoft Authenticator app. This step is required for the shared device SSO experience.
-
Visit Devices > iOS/iPadOS > Configuration Profiles.
-
Create a new profile of the type "Templates" and then select Device features.
-
Enter a profile name such as "Shared Mode SSO Extension".
-
-
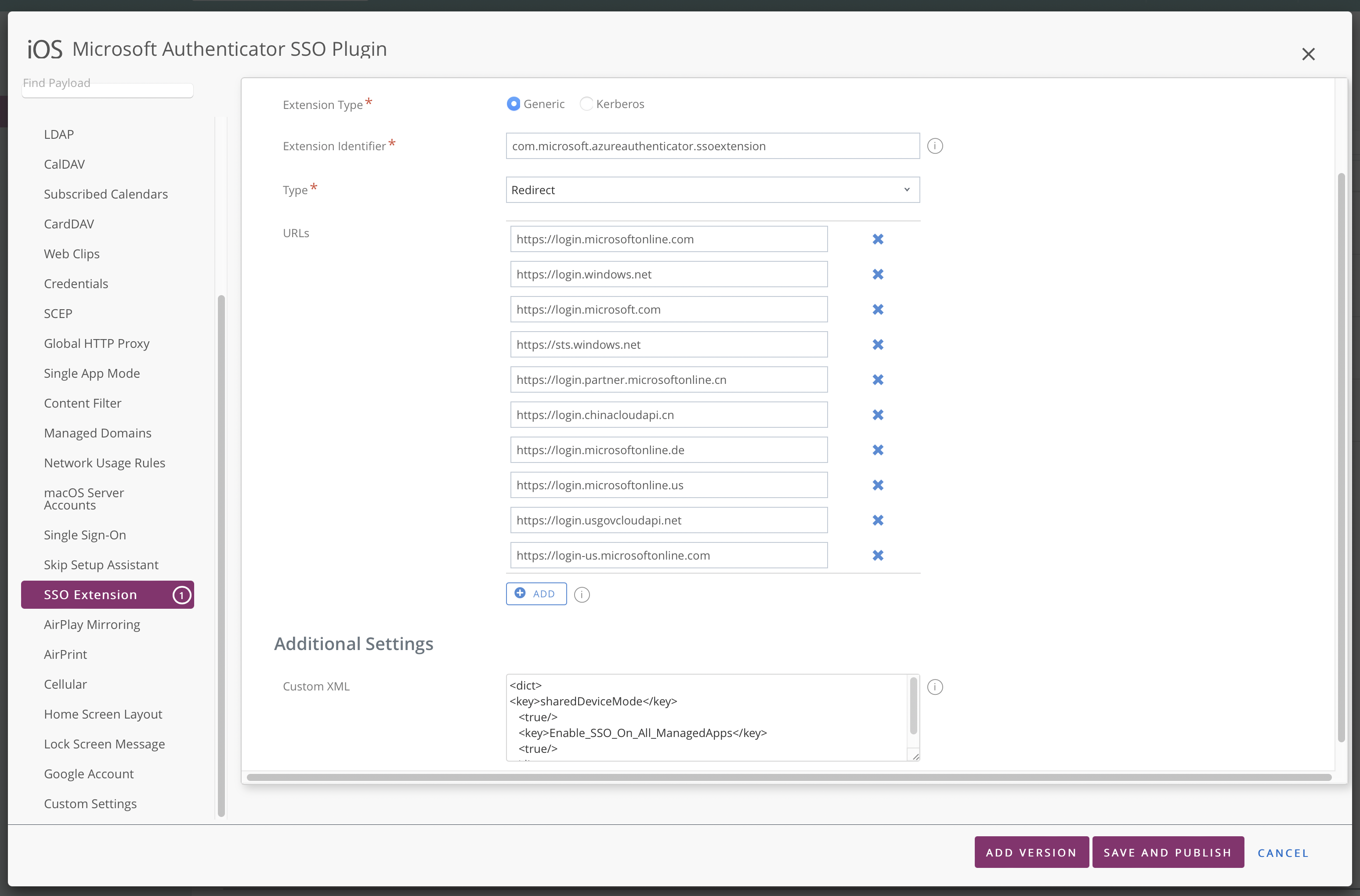
On the next screen, scroll down to Single sign-on app extension.
Select an SSO app extension type of Microsoft Entra ID and enable shared device mode.
-
In the Additional configuration section, add a key:
device_registration String {{DEVICEREGISTRATION}}
sharedDeviceMode String true
-
Configure the rest of the policy to meet your organization's needs. Assign the policy to All devices.
-
Use the enrollmentProfileName assignment filter you created in Step 3 to assign this profile to your group of shared devices.
For other MDMs, there is a little more work to create the profile, but the work is straightforward. Microsoft has documented the generic requirements.
For example, here’s a screenshot of the proper configuration in Omnissa Workspace ONE.
Click to enlarge
Enable Azure for Mobile Access Management Integration
In Azure, create an App Registration to allow Mobile Access Management API access.
If you have already integrated Intune with Mobile Access Management, you may reuse the app you previously created. Just be sure to add the permission User.Read to the app.
-
Log into your Azure tenant at portal.azure.com.
-
Search for the service App registrations.
Click to enlarge
-
Create a new registration.
Click to enlarge
-
Name the application “MAM API Access” or something similar.
-
From the Supported account types list, select Accounts in this organizational directory only. This is the most limited account type.
Click to enlarge
-
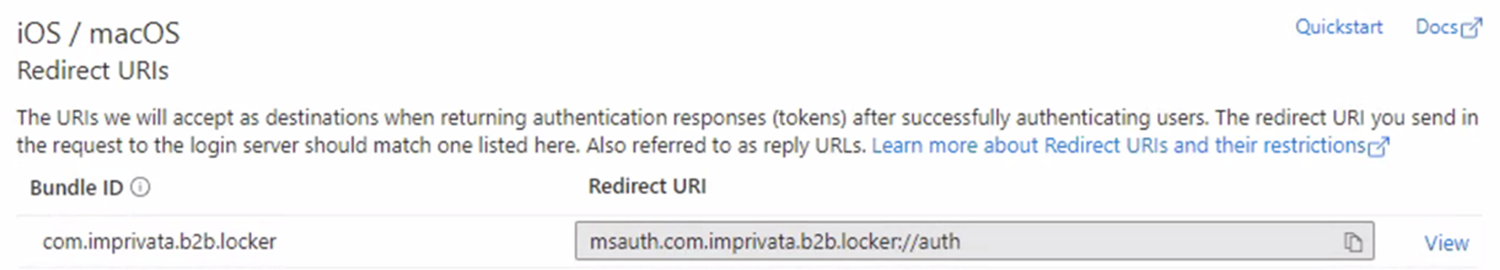
In the Redirect URI box, type msauth.com.imprivata.b2b.locker://auth.
Click to enlarge
-
Click OK to create the application.
-
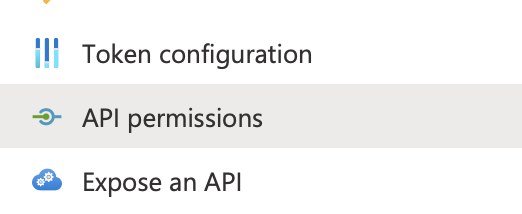
In the vertical navigation bar, select API permissions.
Click to enlarge
-
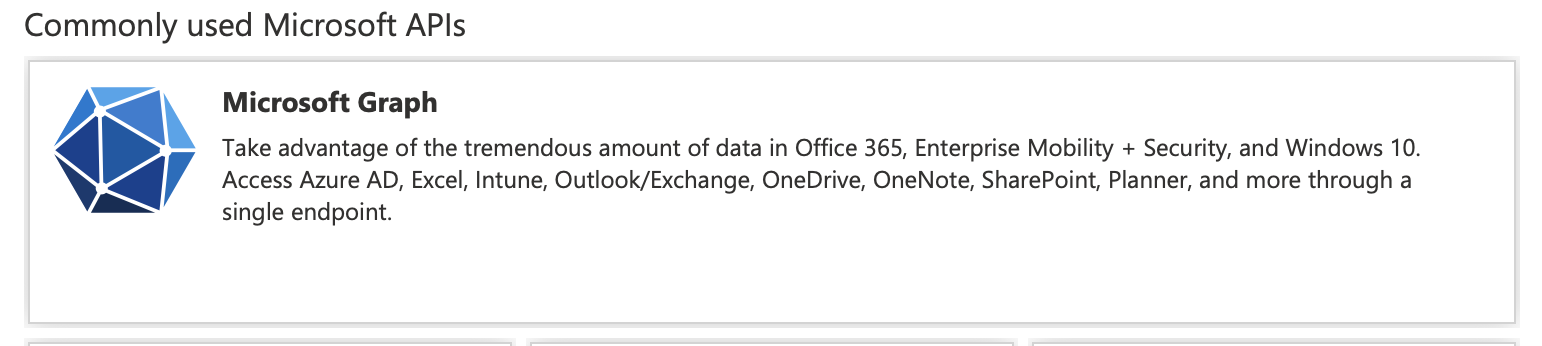
Select the Microsoft Graph API.
Click to enlarge
-
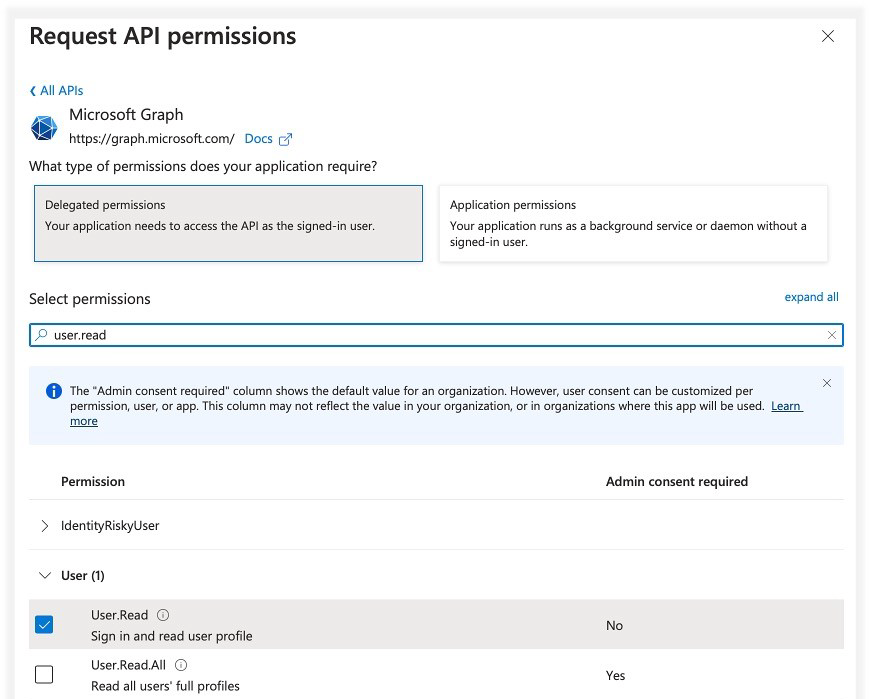
Select Delegated permissions.
Click to enlarge
-
Add permissions for: User.Read.
-
Click Add Permissions.
-
Now that you have created the application, you need to grant permissions to it.
At the top of the permission list is an action Grant admin consent for <company name>.
Click to enlarge
-
Consent to allow the application to access your Azure AD registered devices.
-
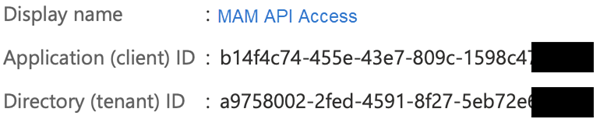
In the vertical navigation bar, click Overview.
-
Copy both the Application (client) ID and the Directory (tenant) IDs to a safe place.
You will use these in the next task.
Click to enlarge
Configure Imprivata Locker iOS
Add a Locker Custom Option with the Azure keys for Imprivata Locker iOS.
-
In MAM’s admin console, navigate to Admin > Check Out > Locker Custom Options, click Configure.
Locker Custom Options are applied after the device is next checked in, when the device is locked and not actively performing any actions.
-
In the Locker Custom Options field, enter the Azure key/value pairs in JSON format and click Save.
Copy"AzureClientID": "<yourAzureApplicationID>"
"AzureTenantID": "<yourAzureDirectoryID>"
"AzureGraphEndpoint": "https://graph.microsoft.com/"
"AzureSignInEnabled": true
"AzureSignOutDelay": 10
"AzureSignOutEnabled": truewhere
-
<yourAzureApplicationID> is the Azure application ID you saved in the previous step.
-
<yourAzureDirectoryID> is the Azure directory ID you saved in the previous step.
-
AzureSignInEnabled specifies whether sign in is enabled using Microsoft’s authentication system. Default is true.
-
AzureSignOutDelay is the number of seconds to delay sign out. Default is 10.
-
AzureSignOutEnabled specifies whether sign out is enabled using Microsoft’s authentication system. Default is true.
-
If you already have Locker Custom Options defined for other MAM features, add the key/value pairs for this feature to your JSON as additional lines:
Example
Copy"AzureClientID": "9999999-abcd-1234-1111111"
"AzureTenantID": "8888888-2222-3333-5555"
"AzureGraphEndpoint": "https://graph.microsoft.com/"
"AzureSignInEnabled": true
"AzureSignOutDelay": 10
"AzureSignOutEnabled": true -