Configure Trusted Communication to the Imprivata Appliance
Beginning with Imprivata MDA 7.15, Imprivata has added the ability to establish a more secure connection between Imprivata MDA and an Imprivata appliance by requiring FQDN addressing rather than IP address and a valid server certificate.
Trust between Imprivata MDA and the Imprivata appliance is achieved by one of the following methods:
-
The Imprivata appliance is configured with a certificate signed by a trusted public Certificate Authority (CA), such as DigiCert or Verisign. For more information on the appliance certificate, see the Imprivata Enterprise Access Management online help.
-
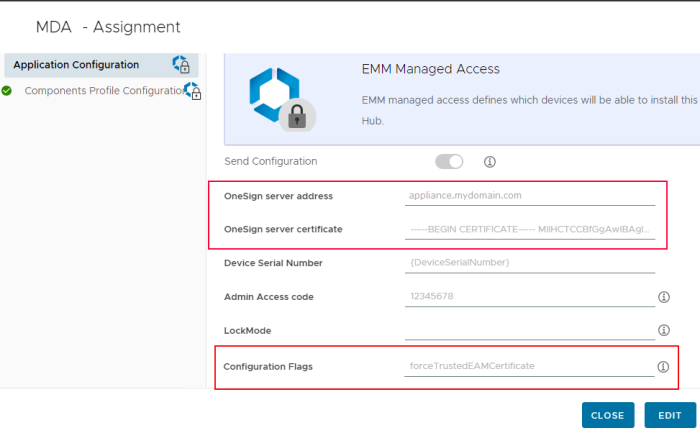
The Imprivata appliance is configured with a self-signed certificate. That certificate is added to an allowlist in Imprivata MDA through the AppConfig parameter "OneSign server certificate" in the MDM.
-
The Imprivata appliance is configured with a certificate that is signed by the customer's Certificate Authority. The certificate signed by the customer's Certificate Authority is added to an allowlist in Imprivata MDA through the AppConfig parameter "OneSign server certificate" in the MDM.
What to Expect
Previous releases of Imprivata MDA (7.14 and earlier) by default allowed untrusted communication with the Imprivata appliance.
With Imprivata MDA 7.15, customers will have the ability to define a more secure connection between the mobile device and the Imprivata appliance, but this is an optional capability in 7.15.
Beginning with Imprivata MDA 7.17, the most secure settings will be the default, so it is important to be familiar with the new settings and try them out ahead of time, if possible.
Imprivata MDA introduced two new AppConfig keys:
-
ConfigFlags allowUntrustedEAMCertificate
-
allowUntrustedEAMCertificate is enabled by default in Imprivata MDA 7.15.
There is no need for additional configuration in Imprivata MDA or in your MDM.
-
Allows communication with an Imprivata appliance that contains a self-signed certificate, or any expired or invalid certificate.
-
This communication is considered as not secure, but allows for backward compatibility and to support cases where a customer may need to use it for a limited time while they resolve any Imprivata appliance certificate issues.
-
Use either allowUntrustedEAMCertificate or forceTrustedEAMCertificate, not both.
-
-
ConfigFlags forceTrustedEAMCertificate
-
Use forceTrustedEAMCertificate to enable the trusted communication with the Imprivata appliance.
Allows you to check whether the EAM certificate is configured correctly and the deployment will work well with future Imprivata MDA releases.
-
Imprivata MDA will only communicate with the Imprivata appliance if the server has a certificate that is either a trusted Certificate Authority (CA) certificate, a customer CA signed certificate, or a self-signed certificate that has been uploaded to the Android system on the device.
Follow the steps below for using the AppConfig parameter "OneSign server certificate" to upload the certificate.
-
If an Imprivata appliance certificate expires, Imprivata MDA will not communicate with the Imprivata appliance.
-
-
Using "OneSign server certificate". This AppConfig parameter allows the appliance's certificate to be uploaded to the MDM when deploying Imprivata MDA to a device.
See the Imprivata MDAAppConfig Reference for supported MDM AppConfig keys.
Future Considerations
In future releases of Imprivata MDA, the forceTrustedEAMCertificate setting will be mandatory and enabled by default.
It is important to test your Imprivata MDA environment with the forceTrustEAMCertificate setting, before the setting becomes mandatory in a future release.
It will help you determine and resolve any issues with your Imprivata appliance certificate.
Configure the MDM AppConfig
Upload the Imprivata Appliance Certificate to the MDM
Some MDMs require that you upload the appliance's .CER certificate file to the MDM via a device configuration profile.
Other MDMs require that you paste the full text of the certificate into the OneSign server certificate AppConfig field, include the -------- BEGIN CERTIFICATE ----------- and --------- END CERTIFICATE --- comments.
For more information, see your MDM documentation.
Enable the Trusted Communication via AppConfig key
To enable the trusted communication with the Imprivata appliance, add the following key:
-
The AppConfig Configuration Key field for this feature is "ConfigFlags".
-
The AppConfig Value Type for this feature is "String".
-
The AppConfig Value is forceTrustedEAMCertificate.
Example - Omnissa Workspace ONE